Azure for Active Directory: 7 Powerful Insights You Must Know
Thinking about upgrading your identity management? Azure for Active Directory isn’t just a cloud version of an old system—it’s a game-changer. Discover how it transforms security, scalability, and user management in modern enterprises.
Understanding Azure for Active Directory: The Modern Identity Backbone

Azure for Active Directory, often referred to as Azure AD, is Microsoft’s cloud-based identity and access management service. It’s not merely a migration of on-premises Active Directory (AD) to the cloud but a reimagined platform built for the era of hybrid work, multi-device access, and zero-trust security models. While traditional AD focuses on managing users and resources within a local network, Azure AD extends that capability to the cloud, enabling seamless access to thousands of SaaS applications like Microsoft 365, Salesforce, and Dropbox.
What Is Azure for Active Directory?
Azure for Active Directory is a comprehensive identity-as-a-service (IDaaS) solution that provides single sign-on (SSO), multi-factor authentication (MFA), conditional access, and identity protection. It acts as the central hub for user authentication and authorization across cloud and on-premises environments. Unlike its on-premises counterpart, Azure AD is designed from the ground up for internet-scale operations, supporting millions of users and devices globally.
- It authenticates users across cloud apps and services.
- It integrates with on-premises AD via Azure AD Connect.
- It supports modern authentication protocols like OAuth 2.0, OpenID Connect, and SAML.
One of the most powerful aspects of Azure for Active Directory is its ability to unify identity management across hybrid environments. Whether your users are logging in from a corporate laptop in the office or a personal smartphone from a remote location, Azure AD ensures secure, policy-driven access.
Evolution from On-Premises AD to Cloud Identity
The shift from traditional Active Directory to Azure for Active Directory reflects a broader transformation in IT infrastructure. On-premises AD was designed for a world where networks were trusted, and users accessed resources from within a physical office. Today, with remote work and cloud applications, that model is no longer sufficient.
Microsoft recognized this shift early and developed Azure AD as a cloud-native identity platform. It doesn’t replace on-premises AD overnight but complements it through hybrid identity solutions. Over time, many organizations are moving toward a cloud-first or cloud-only model, reducing dependency on domain controllers and Group Policy Objects (GPOs).
“Azure AD is not just the cloud version of Active Directory—it’s the future of identity management.” — Microsoft Ignite Keynote, 2022
This evolution allows IT teams to offload infrastructure management, reduce latency, and improve user experience through faster logins and self-service capabilities.
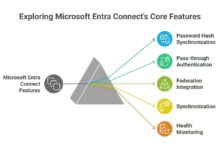
Key Features of Azure for Active Directory
Azure for Active Directory offers a robust set of features that go far beyond basic user authentication. These capabilities are designed to meet the demands of modern enterprises, from small businesses to global corporations. Let’s explore the core functionalities that make Azure AD a leader in identity management.
Single Sign-On (SSO) Across Applications
One of the most user-facing benefits of Azure for Active Directory is single sign-on. With SSO, users can access multiple applications—both cloud and on-premises—with just one set of credentials. This eliminates password fatigue and reduces helpdesk tickets related to forgotten passwords.
- Supports over 2,600 pre-integrated SaaS apps.
- Enables seamless access to custom line-of-business apps.
- Integrates with third-party identity providers via federation.
For example, a user can log in once and gain access to Microsoft 365, Salesforce, Workday, and internal portals without re-entering credentials. This not only improves productivity but also strengthens security by reducing the temptation to reuse passwords.
Multi-Factor Authentication (MFA) and Conditional Access
Security is at the heart of Azure for Active Directory. Multi-factor authentication adds an extra layer of protection by requiring users to verify their identity using a second method—such as a phone call, text message, or authenticator app.
Conditional Access takes this further by enforcing policies based on risk, location, device compliance, and user behavior. For instance, you can configure a policy that:
- Blocks access from unfamiliar countries.
- Requires MFA when accessing sensitive data from unmanaged devices.
- Allows access only from compliant devices enrolled in Intune.
These policies are built using a simple if-then logic in the Azure portal, making it easy for administrators to implement zero-trust principles without writing code.
Identity Protection and Risk-Based Policies
Azure for Active Directory includes advanced threat detection through Identity Protection. This feature uses machine learning to detect suspicious activities such as sign-ins from anonymous IPs, leaked credentials, or impossible travel (e.g., logging in from New York and London within minutes).
When a risky sign-in is detected, Azure AD can automatically trigger actions like:
- Blocking the sign-in attempt.
- Requiring password reset.
- Enforcing MFA.
According to Microsoft, organizations using Identity Protection see a 99.9% reduction in account compromise incidents. This proactive approach to security is a major reason why Azure for Active Directory is trusted by enterprises worldwide.
Hybrid Identity: Bridging On-Premises and Cloud
For many organizations, a complete migration to the cloud isn’t feasible overnight. That’s where hybrid identity comes in. Azure for Active Directory supports seamless integration between on-premises Active Directory and the cloud, allowing businesses to maintain existing infrastructure while gradually adopting cloud benefits.
Using Azure AD Connect for Synchronization
Azure AD Connect is the primary tool for synchronizing user identities from on-premises AD to Azure AD. It ensures that user accounts, passwords, and group memberships are kept in sync across environments.
- Supports password hash synchronization, pass-through authentication, and federation.
- Allows selective synchronization of organizational units (OUs).
- Provides health monitoring and alerting.
For example, when an HR system creates a new employee account in on-premises AD, Azure AD Connect automatically syncs that account to the cloud, enabling immediate access to cloud resources without manual intervention.
Password Hash Sync vs. Pass-Through Authentication
When setting up hybrid identity, administrators must choose between password hash synchronization (PHS) and pass-through authentication (PTA). Both have pros and cons:
- Password Hash Sync: Stores a cryptographic hash of the user’s password in Azure AD. Users can authenticate directly against Azure AD, even if on-premises servers are down.
- Pass-Through Authentication: Validates the user’s password against on-premises AD in real time. No password hashes are stored in the cloud, enhancing security.
Microsoft recommends PTA for organizations prioritizing security, while PHS is ideal for those needing high availability and disaster recovery. You can learn more about these options in Microsoft’s official documentation: Azure AD Authentication Methods.
Federation with AD FS
For organizations with existing investments in Active Directory Federation Services (AD FS), Azure for Active Directory supports federation. This allows users to authenticate against on-premises AD FS servers while accessing cloud applications.
However, Microsoft is encouraging a shift away from AD FS toward cloud-native authentication methods like PTA and PHS, citing benefits such as reduced infrastructure costs, easier management, and better scalability.
“Federation is still supported, but the future is in cloud authentication.” — Microsoft Azure Blog
Security and Compliance in Azure for Active Directory
In today’s threat landscape, identity is the new perimeter. Azure for Active Directory plays a critical role in securing enterprise environments by enforcing strong authentication, monitoring for anomalies, and ensuring compliance with regulatory standards.
Zero Trust Architecture and Azure AD
The zero trust model assumes that no user or device should be trusted by default, even if they are inside the corporate network. Azure for Active Directory is a foundational component of Microsoft’s zero trust framework.
- Verifies user identity every time they access a resource.
- Validates device compliance before granting access.
- Uses adaptive policies to respond to risk in real time.
By implementing zero trust with Azure AD, organizations can significantly reduce the attack surface and prevent lateral movement by attackers who have compromised a single account.
Audit Logs and Monitoring Capabilities
Transparency and accountability are essential for security and compliance. Azure for Active Directory provides comprehensive audit logs that track user sign-ins, administrative changes, and policy updates.
- Logs include timestamps, IP addresses, user agents, and result codes.
- Data can be exported to SIEM tools like Azure Sentinel or Splunk.
- Custom alerts can be set for suspicious activities.
For example, if an admin deletes a user account, the action is logged with the admin’s identity and the time of deletion. This helps meet compliance requirements for SOX, HIPAA, GDPR, and other regulations.
Compliance Certifications and Data Residency
Microsoft invests heavily in ensuring Azure for Active Directory meets global compliance standards. The service is certified for ISO/IEC 27001, SOC 1/2/3, GDPR, HIPAA, and more.
Data residency is another key concern. Azure AD allows organizations to specify where their data is stored, ensuring compliance with local data protection laws. For instance, European customers can ensure that their identity data remains within the EU.
More details on compliance can be found in the Microsoft Compliance Manager.
Deployment Models: Cloud-First, Hybrid, or Cloud-Only?
Organizations have different needs when it comes to identity management. Azure for Active Directory supports multiple deployment models, allowing businesses to choose the approach that best fits their infrastructure and strategy.
Cloud-First Strategy with On-Premises Integration
A cloud-first strategy means prioritizing cloud solutions while maintaining some on-premises systems. In this model, Azure AD becomes the primary identity provider, with on-premises AD serving legacy applications.
- User lifecycle management is done in Azure AD.
- On-premises AD is used for backward compatibility.
- Group Policy is gradually replaced with Intune policies.
This approach is ideal for organizations undergoing digital transformation and wanting to reduce dependency on physical servers.
Fully Cloud-Only Environments
Some organizations, especially startups or remote-first companies, operate entirely in the cloud. In a cloud-only model, there is no on-premises AD. All users, groups, and policies are managed directly in Azure for Active Directory.
- No need for domain controllers or AD FS servers.
- Users are created and managed in the Azure portal.
- Devices are joined to Azure AD instead of on-premises domains.
This model offers maximum agility and scalability, with minimal IT overhead. It’s particularly effective when combined with Microsoft 365 and Intune for endpoint management.
Hybrid Identity with Seamless SSO
For enterprises with complex legacy systems, hybrid identity remains the most practical option. Azure AD Connect enables seamless single sign-on, allowing users to access cloud apps without re-entering credentials, just as they would in a traditional domain environment.
Seamless SSO works by leveraging the user’s domain-joined device and Kerberos ticket to authenticate them silently to Azure AD. This provides a smooth user experience while maintaining security.
Learn more about deployment options at Azure AD Hybrid Identity Documentation.
Managing Users and Devices with Azure for Active Directory
Effective identity management isn’t just about users—it’s about devices too. Azure for Active Directory provides tools to manage both, ensuring that only authorized users on compliant devices can access corporate resources.
User Lifecycle Management
Azure AD simplifies user provisioning and deprovisioning through automated workflows. When a new employee joins, their account can be created in Azure AD and automatically granted access to the apps they need.
- Supports role-based access control (RBAC).
- Integrates with HR systems via Azure AD Connect or SCIM.
- Enables self-service password reset and group management.
When an employee leaves, their account can be disabled or deleted, immediately revoking access to all connected services. This reduces the risk of orphaned accounts being exploited by attackers.
Device Registration and Compliance Policies
With the rise of BYOD (Bring Your Own Device), managing endpoints has become more complex. Azure for Active Directory supports device registration, allowing personal and corporate devices to be recognized and managed.
- Devices can be Azure AD-joined, hybrid Azure AD-joined, or registered.
- Conditional Access policies can require device compliance.
- Integration with Microsoft Intune enables full device management.
For example, a policy can block access to email from a device that doesn’t have encryption enabled or is running an outdated OS version.
Self-Service Features for End Users
Azure for Active Directory empowers users with self-service tools, reducing the burden on IT staff. Features include:
- Self-Service Password Reset (SSPR): Users can reset their passwords without calling the helpdesk.
- Group Management: Users can create and manage security groups based on admin-defined policies.
- Access Reviews: Managers can periodically review who has access to which resources.
According to Microsoft, organizations using SSPR see a 40% reduction in helpdesk calls related to password issues.
Cost, Licensing, and Planning for Azure for Active Directory
Understanding the cost structure and licensing options is crucial for planning a successful Azure for Active Directory deployment. While there is a free tier, most enterprises require premium features that come with paid licenses.
Free vs. Premium Tiers (P1 and P2)
Azure for Active Directory offers multiple licensing tiers:
- Free: Includes basic SSO, 50,000 objects, and group-based access.
- Premium P1: Adds MFA, conditional access, hybrid identity, and self-service password reset.
- Premium P2: Includes Identity Protection, privileged identity management (PIM), and advanced reporting.
Most organizations start with P1 and upgrade to P2 for enhanced security. Licensing is per user per month, and it’s often bundled with Microsoft 365 plans.
Integration with Microsoft 365 and Other Services
Azure for Active Directory is deeply integrated with Microsoft 365. In fact, every Microsoft 365 subscription includes Azure AD capabilities. This integration enables features like:
- Automatic user provisioning for Teams, SharePoint, and Exchange Online.
- Conditional access for protecting sensitive documents.
- Identity governance for compliance audits.
It also integrates with other Azure services like Azure Virtual Desktop, Azure API Management, and Azure Logic Apps, making it a central component of the Microsoft cloud ecosystem.
Planning Your Migration to Azure AD
Migrating to Azure for Active Directory requires careful planning. Key steps include:
- Assessing current AD environment and application dependencies.
- Choosing the right authentication method (PHS, PTA, or federation).
- Designing conditional access policies and security baselines.
- Training IT staff and end users on new workflows.
Microsoft provides a Hybrid Identity Planning Guide to help organizations navigate this process.
What is Azure for Active Directory?
Azure for Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. It enables single sign-on, multi-factor authentication, and secure access to cloud and on-premises applications. It is not a direct replacement for on-premises Active Directory but a modern identity platform designed for hybrid and cloud-first environments.
How does Azure AD differ from on-premises Active Directory?
On-premises Active Directory is designed for managing users and resources within a local network using domain controllers and Group Policy. Azure AD is cloud-native, protocol-based (OAuth, SAML), and focused on securing access to cloud applications. It supports modern authentication, conditional access, and identity protection, making it ideal for remote work and zero-trust security.
Can I use Azure AD without on-premises Active Directory?
Yes, Azure for Active Directory can be used in a cloud-only model. Organizations can create and manage users, groups, and devices directly in Azure AD without any on-premises infrastructure. This is common for startups, remote teams, and businesses fully adopting Microsoft 365.
What are the main security features of Azure AD?
Azure AD includes multi-factor authentication (MFA), conditional access policies, Identity Protection for risk detection, privileged identity management (PIM), and audit logging. These features help enforce zero-trust principles, detect threats, and ensure compliance with regulatory standards.
How much does Azure for Active Directory cost?
Azure AD has a free tier with basic features. Premium P1 costs $6/user/month and includes MFA and conditional access. Premium P2 is $9/user/month and adds Identity Protection and PIM. Licensing is often included in Microsoft 365 subscriptions.
Adopting Azure for Active Directory is more than a technical upgrade—it’s a strategic move toward a secure, scalable, and user-friendly identity management system. Whether you’re running a hybrid environment or going fully cloud-native, Azure AD provides the tools to protect your organization while enabling seamless access for users. With robust security features, deep integration with Microsoft 365, and flexible deployment options, it’s no wonder that millions of organizations trust Azure for Active Directory as their identity backbone. The future of identity is in the cloud, and Azure AD is leading the way.
Recommended for you 👇
Further Reading: